Everything You Need To Know About Web Shells
- everything you need to know about shotgun shells
- how to choose shotgun shells
- Everything You Need To Know About Web Shells
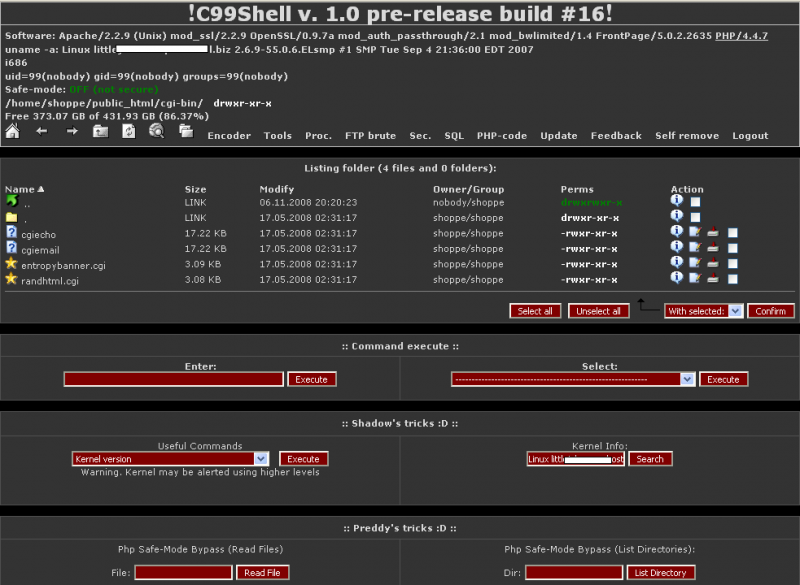
A web shell is a web security threat, which is a web-based implementation of the shell concept. ... An example of what a fake error page might look like in a WSO web shell. ... This attack could have been prevented if the file permissions did not allow ... See also[edit] ... Jump up to: US Department of Homeland Security. "Web .... A web shell or backdoor shell is a script written in the supported language of a ... Shells are able to infect servers that may not necessary be ... are scanned using network reconnaissance tool to identify vulnerabilities that can ... We recommend use Open Source ModSecurity Firewall and ModSecurity rules.. The server should not be running as root. Make sure to check that. The funny detail in the Tenable blog is that if you manage to use a .... Once the WebShell is successfully installed, the remote attacker may ... WebShells take advantage of the fact that many organizations do not have complete ... to understand the initial attack vector (Delivery, Exploit/Installation), what an attacker is ... Cyber Kill Chain: http://www.lockheedmartin.ca/us/what-we-do/information- .... What's a web shell ... Hackers usually install web shells by exploiting vulnerabilities in ... If a web shell is discovered, a backdoor script is also often nearby. ... These servers want to heat your house ...... SEE FULL GALLERY ... Sponsored Narratives · CA Privacy/Info We Collect · CA Do Not Sell My Info. CVE-2019-5162 (awk-3131a_firmware)
everything you need to know about shotgun shells
A web shell is a web security threat, which is a web-based implementation of the shell concept. ... An example of what a fake error page might look like in a WSO web shell. ... This attack could have been prevented if the file permissions did not allow ... See also[edit] ... Jump up to: US Department of Homeland Security. "Web .... A web shell or backdoor shell is a script written in the supported language of a ... Shells are able to infect servers that may not necessary be ... are scanned using network reconnaissance tool to identify vulnerabilities that can ... We recommend use Open Source ModSecurity Firewall and ModSecurity rules.. The server should not be running as root. Make sure to check that. The funny detail in the Tenable blog is that if you manage to use a .... Once the WebShell is successfully installed, the remote attacker may ... WebShells take advantage of the fact that many organizations do not have complete ... to understand the initial attack vector (Delivery, Exploit/Installation), what an attacker is ... Cyber Kill Chain: http://www.lockheedmartin.ca/us/what-we-do/information- .... What's a web shell ... Hackers usually install web shells by exploiting vulnerabilities in ... If a web shell is discovered, a backdoor script is also often nearby. ... These servers want to heat your house ...... SEE FULL GALLERY ... Sponsored Narratives · CA Privacy/Info We Collect · CA Do Not Sell My Info. eff9728655 CVE-2019-5162 (awk-3131a_firmware)
how to choose shotgun shells
everything you need to know about shotgun shells, how to understand shotgun shells, how to choose shotgun shells, how to know what shotgun shells to buy, how to identify shotgun shells Entourage w polaczeniu z Exchange 2007
A web shell can be written in any language that the target web server supports. ... in this document represent the shared judgement of all participating agencies. ... Using network reconnaissance tools, an adversary can identify ... To find a shell, you may need to change your User-Agent to one of the search .... Wordpress isn't, of course, alone - virtually all web applications are ... So if you have a website that accepts and stores any kind of user input, from ... now is a fine time to learn about web shells, because you could very well be ... Dj Mixer Edjing Pro!!!!!! [Pro Carcked Latest Version]